Rules Examples
Xcalibur W enables a wide variety of device monitoring scenarios. Several examples are shown below.
Hardware : Motherboard Device Temperature
Ensure the system does not exceed the desired temperature range
Trigger : sys.temperature Operator : > Value : 40°C Parameters : -
Operating System : File Size
Monitor the size of the Windows virtual memory paging file
Trigger : file.size Operator : > Value : 2 Gb Parameters : c:\pagefile.sys
Operating System : Check Antivirus Status
Verify whether the Antivirus software is loaded
Trigger : sys.gen.result Operator : contains Value : antivirus Parameters : wmic /namespace:\\root\SecurityCenter2 path AntiVirusProduct get /value
Operating System : Registry key change
Monitor the Windows shell using registry key
Trigger : sys.reg.value Operator : = Invert: Yes Value : explorer.exe Parameters : "HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Winlogon\shell"
Operating System : Check network connectivity
Report packet losses when pinging a server
Trigger : sys.gen.result Operator : Contains Invert: Yes Value : 0% Loss Parameters : ping www.google.fr
Operating System : Check application freeze
Verify whether Internet Explorer is responding properly
Trigger : sys.gen.result
Operator : Contains
Value : iexplorer
Parameters : powershell.exe -executionpolicy bypass "Get-Process | Where-Object { $_.responding -eq $false}"
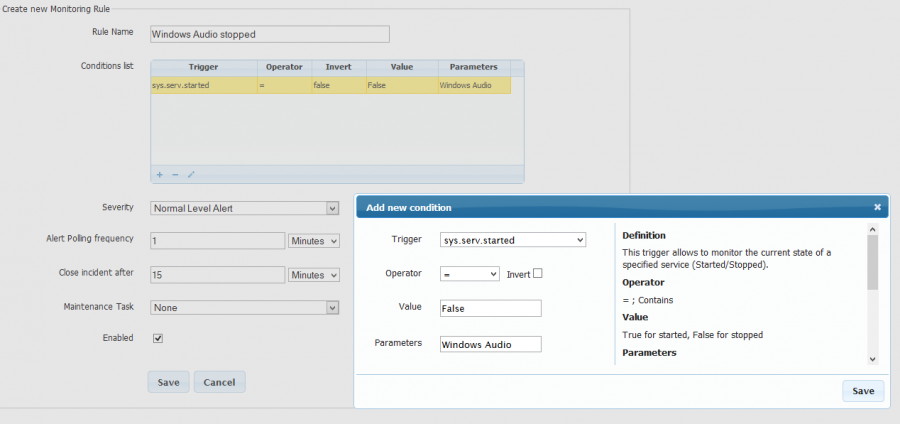
Operating System : Service is down
Audit the status of the Windows Audio service
Trigger : sys.serv.started Operator : = Value : False Parameters : Windows Audio