User Tools
You are here: Introduction » Installation Guide » Server Software Installation » Manual Installation » Forbid HTTP access
Sidebar
installation_guide:server_software_installation:manual_installation:forbid_http_access
Forbid HTTP access
By default, Administrator can log in to the Xcalibur W server using either HTTP or HTTPS connection. In order to prevent from using unsecure HTTP connection, you will need to configure your IIS server to automatically redirect HTTP access attempts to HTTPS. For that purpose, the Microsoft's URL rewriter Module shall be install on IIS.
You can download the URL rewriter module at: http://www.iis.net/downloads/microsoft/url-rewrite
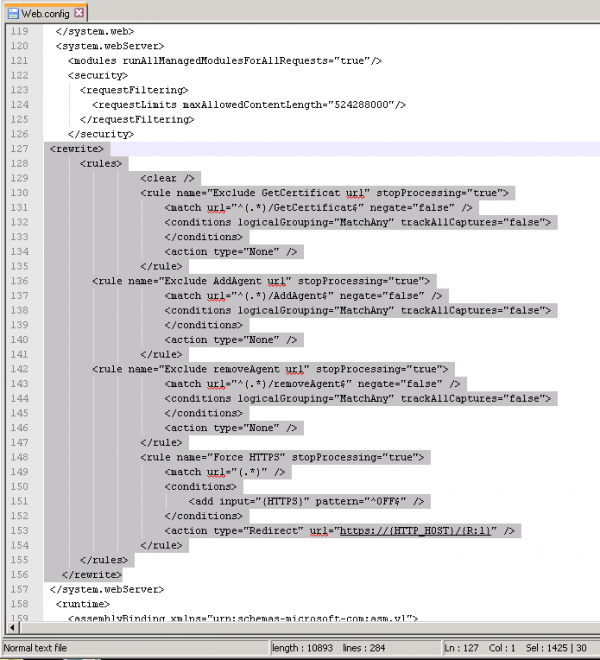
Once installed, you need to edit and add the following lines into the C:\inetpub\wwwroot\XcaliburwMS\web.config
<system.webServer>
<rewrite>
<rules>
<clear />
<rule name="Exclude GetCertificat url" stopProcessing="true">
<match url="^(.*)/GetCertificat$" negate="false" />
<conditions logicalGrouping="MatchAny" trackAllCaptures="false" />
<action type="None" />
</rule>
<rule name="Exclude AddAgent url" stopProcessing="true">
<match url="^(.*)/AddAgent$" negate="false" />
<conditions logicalGrouping="MatchAny" trackAllCaptures="false" />
<action type="None" />
</rule>
<rule name="Exclude removeAgent url" stopProcessing="true">
<match url="^(.*)/removeAgent$" negate="false" />
<conditions logicalGrouping="MatchAny" trackAllCaptures="false" />
<action type="None" />
</rule>
<rule name="Exclude VNC requests" stopProcessing="true">
<match url="/(.*)vnc(.*)" />
<conditions logicalGrouping="MatchAll" trackAllCaptures="false" />
<action type="None" />
</rule>
<rule name="Force HTTPS" stopProcessing="true">
<match url="(.*)" />
<conditions logicalGrouping="MatchAll" trackAllCaptures="false">
<add input="{HTTPS}" pattern="^OFF$" />
</conditions>
<action type="Redirect" url="https://{HTTP_HOST}/{R:1}" />
</rule>
</rules>
</rewrite>
</system.webServer> >
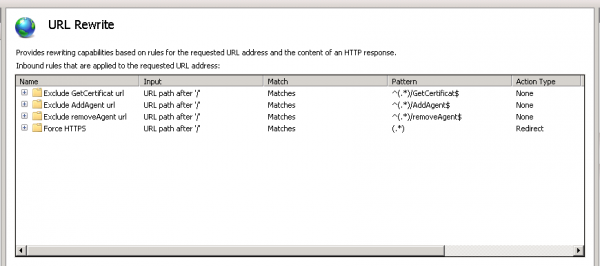
Once done, you can restart IIS service. You can then check that the URL Rewriter rule has been properly been added on IIS management console:
installation_guide/server_software_installation/manual_installation/forbid_http_access.txt · Last modified: 2021/11/21 17:41 (external edit)